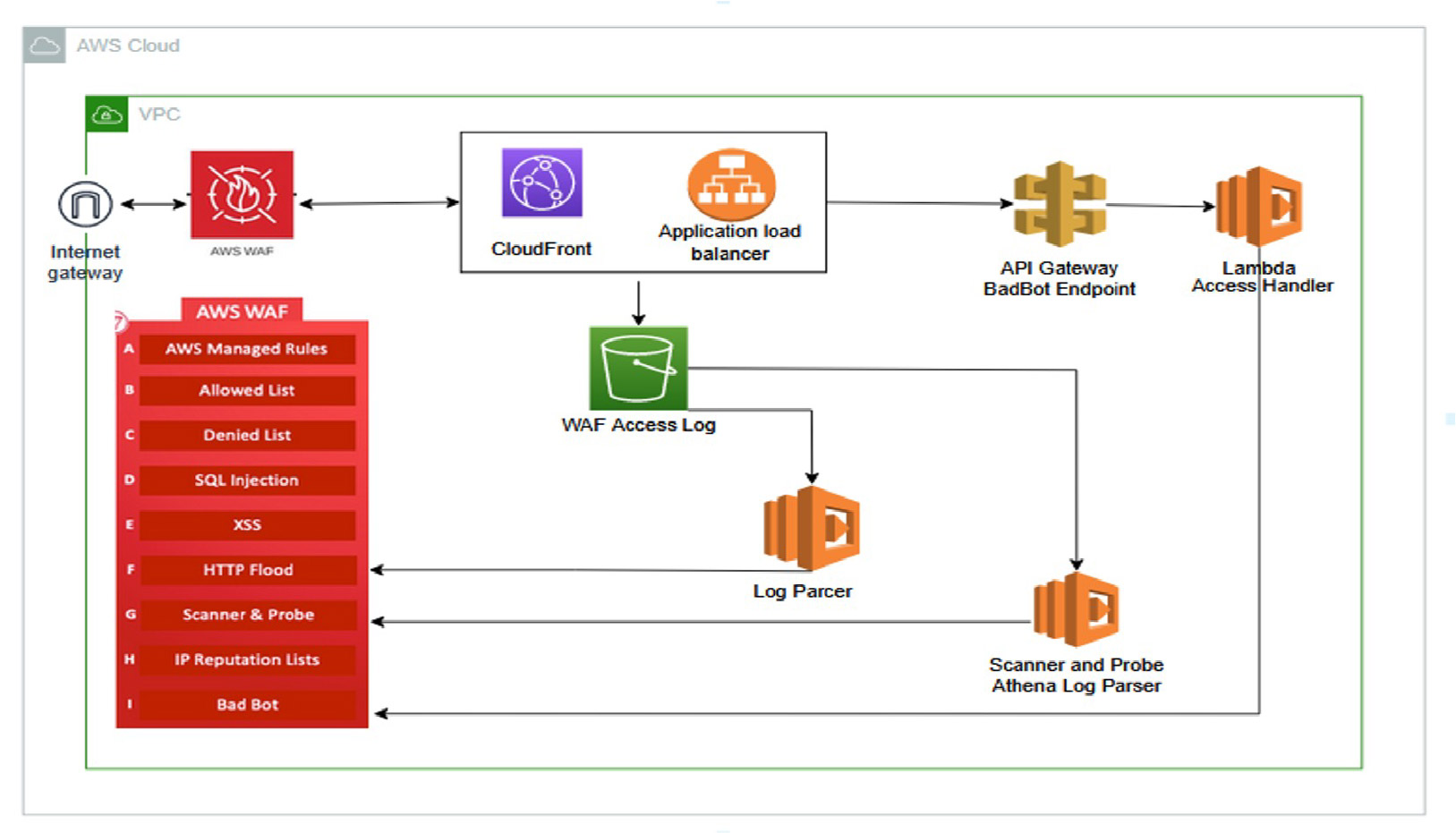
Secure your AWS Workload with our automated Deployment of WAF rule to prevent common known vulnerabilities and cyber threats.
WAF provides security over protecting your workload and prevent the common threats and attack. It also helps to protect resources such Cloud front and Application load balancer by inspecting the web request.
This offering provides automated WAF deployment to protect the workload across AWS.
We use CloudFormation, to perform deployment and it helps protecting the workload from its known common attack surface