
No worries of loosing
Customers

Zero investment on setting up a team to cater cyber security market

25+ Cyber Security Certified Architects works as your extended team

Numerous opportunities to expand with 4x Drag Revenue thru Up-sell & Cross-sell

Free Security Assessment for your customers thru industry-leading tools & technology
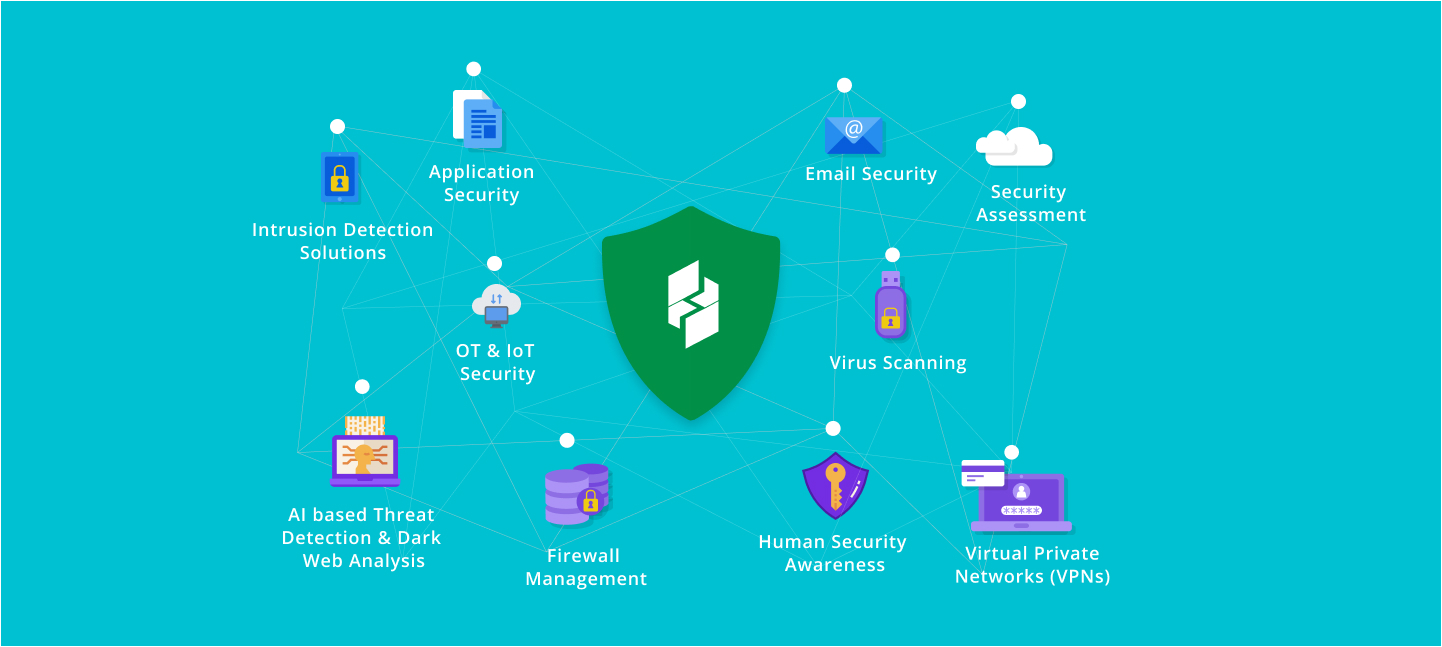
What we can help you with:
Direct communication with security analysts
Tools to help your customer demonstrate compliance
Detection of security threats which will help you to advice preventive solutions
24x7x365 monitoring of customer's networks, endpoints, applications and data from cyber threats
Significant reduction in cost compared to on - premise SOC solution
Off-load resource-intensive security operations to skilled security experts, letting your customers focus on their business